"Innovation and foresight are hard, especially for things we haven't seen."
-- Chenglian
moving beyond "Chat with your Data" to "Autonomous Service Fulfillment"
We have spent the last year mastering Retrieval-Augmented Generation (RAG) - teaching LLMs to know our data.
2026 is the year of Agentic AI - teaching LLMs to act on our services.
However, for Enterprise Architects and Engineering Leaders, the transition from a "Chatbot" to a "Transactional Agent" presents a massive reliability gap. In a production environment, you cannot simply pipe a probabilistic LLM directly into your core banking or trading APIs. The risk of hallucinated parameters or loop failures is too high.
To transform a Service Provider into an AI-Enabled Enterprise, we must move beyond simple 3-tier architectures. We need a dedicated Agentic Stack that enforces a strict Separation of Concerns between reasoning, execution, and fulfillment.
Here is the reference architecture I propose for the next generation of AI services:
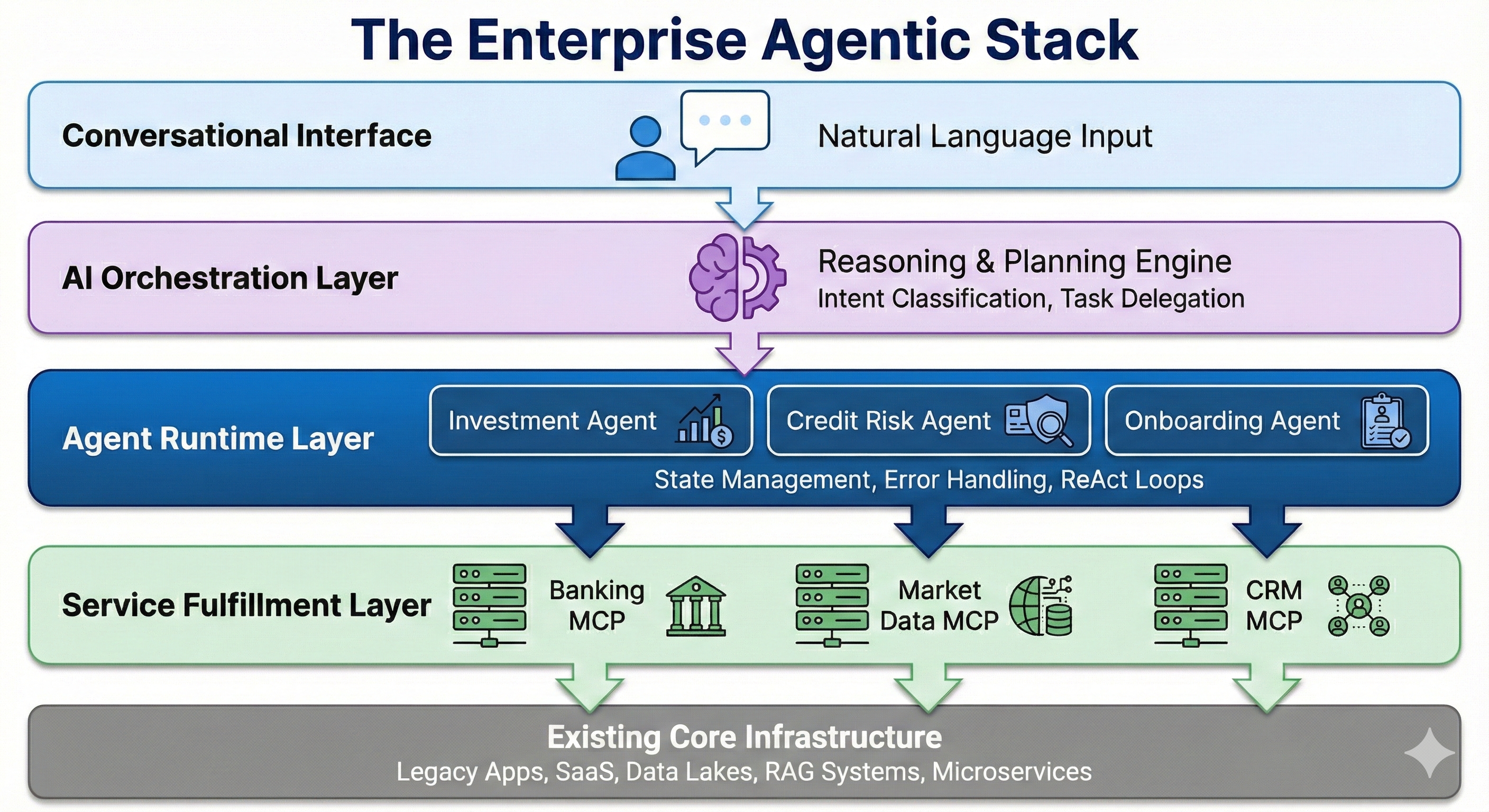
Sitting below the conversational interface, this layer does not perform work. It is purely the reasoning engine.
Role: Intent classification, high-level planning, and decomposition.
Function: It analyzes a user request ("Rebalance my portfolio based on my risk profile"), breaks it down into a dependency graph, and delegates tasks to specialized workers.
This is the "Missing Link" in most current deployments. We cannot expect a single generic LLM to handle state, retries, and domain nuances for every task.
Role: Specialized, stateful execution.
Structure: A runtime hosting a mesh of domain-specific agents (e.g., an Investment Agent, a Credit Risk Agent, an Onboarding Agent).
Function: These agents run dedicated control loops (ReAct: Reason + Act). They handle error recovery, maintain the state of the transaction, and ensure business logic integrity before touching the backend.
This layer represents the evolution of the API Gateway. Instead of brittle, custom-coded integration glue, we deploy a fleet of Model Context Protocol (MCP) Servers.
Role: Deterministic capabilities exposure.
Function: Each MCP Server fronts a specific domain (Banking Core, Market Data, CRM). They expose standardized "tools" that the Agent Runtime layer can discover and invoke safely.
This is where your data and record-keeping systems live.
Crucial Shift: Note that RAG Systems (Vector DBs, Knowledge Bases) now sit here alongside SQL Databases and Legacy Apps.
Why: In an Agentic architecture, RAG is simply another data utility—a "read-only" dependency that the higher-level agents consume to make informed decisions.
By inserting the Agent Runtime between the reasoning brain (Orchestration) and the tools (Fulfillment), we solve the "hallucination in production" problem.
The Orchestrator plans, the Agent Runtime validates and executes, and the MCP Servers fulfill. This is how we move beyond "Chat with your Data" to "Autonomous Service Fulfillment".
Quick Wins for Every Organization in the dynamic world of AI
In the dynamic world of AI, a multitude of opportunities exist, offering readily available solutions with substantial benefits. Even organizations with limited resources or AI experience can harness these accessible options. Let's explore some of the most impactful ways AI can quickly enhance your organization's operations and outcomes.
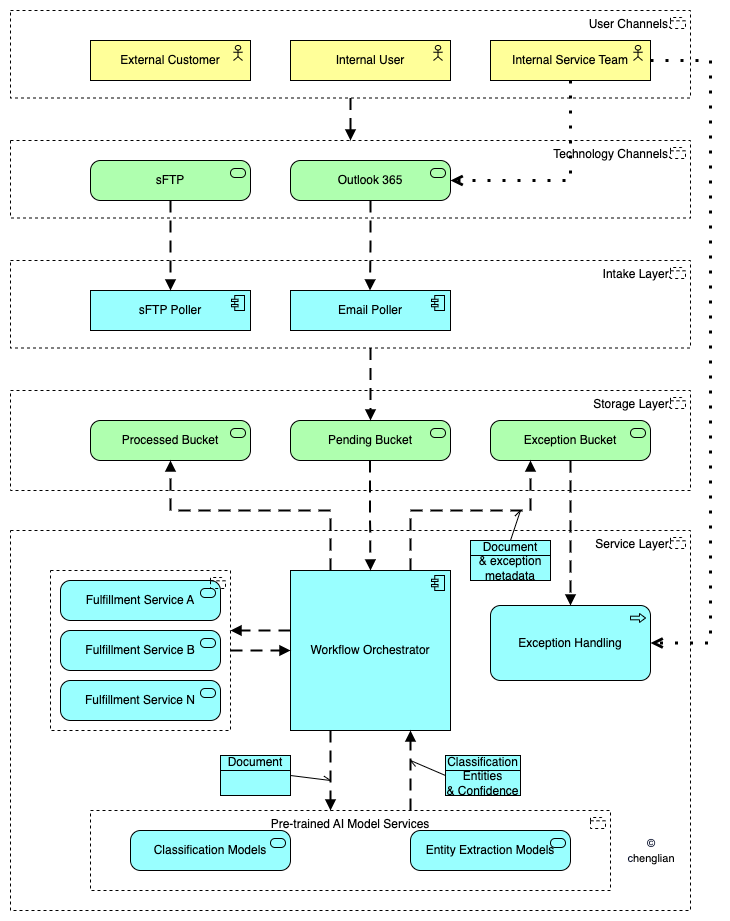
The overwhelming volume of documents modern organizations face can be streamlined with AI-powered automation. By defining classification categories, organizations can automate document classification based on intent, service requests, product categories, customer groups, and more. AI enables the extraction of crucial information like names, dates, and amounts from unstructured documents. This automation can initiate downstream workflows for end-to-end processing. Input can originate from file drops or emails containing attachments. For example, Microsoft Power Automate [1], along with Microsoft prebuilt AI models [2], facilitates invoice and receipt processing, entity extraction, category classification, and more. Microsoft provides versatile AI models as native cloud services. These Azure AI models can also be deployed as container images within your environment, ensuring data security and compliance [3]. Microsoft AI Builder allows organizations to build their own document processing models - tailored to the organization - by training the models with specific sets of documents.
One caveat is that organizations using pre-trained AI models must consider the confidence level of the AI's output. Workflows should be designed to allow for human intervention or extra verification when the confidence level falls below the acceptable risk threshold for the specific use case.
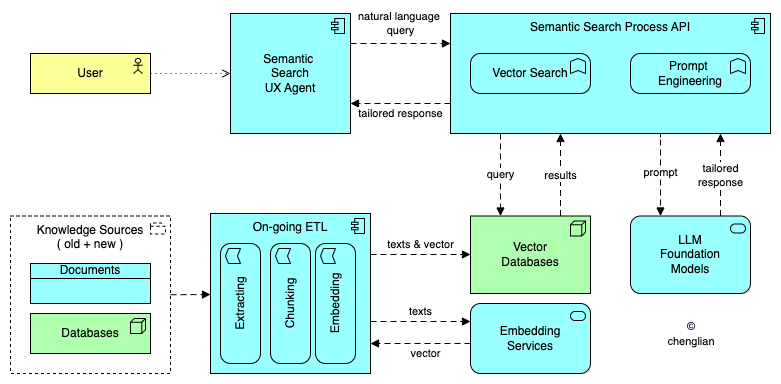
While internal knowledge bases are invaluable, traditional keyword-based search often falls short. By utilizing vector databases and embedding services, organizations can construct semantic search-enabled internal knowledge bases encompassing policies, processes, employee information, technology and product information, and more. User queries, enriched with organization-specific information through prompt engineering, can be seamlessly integrated with LLM models for tailored responses; this is so-called retrieval-augmented generation (RAG). Employees can interact with these engines using natural language for direct resolutions or next-step instructions, effectively replacing level-one support. Similarly, a public-facing knowledge base with semantic search empowers customers to resolve issues independently, enhancing satisfaction and loyalty.
It's important to acknowledge that LLMs, even with RAG, can sometimes generate incorrect or nonsensical responses; apply mitigations where necessary (e.g., response validation, user feedback mechanisms).
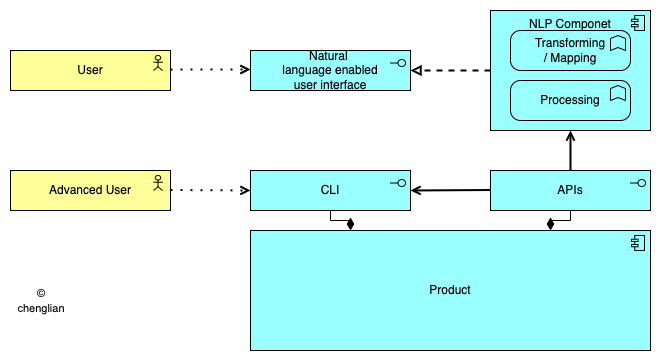
Expanding beyond traditional UI/CLI tools and APIs, organizations can incorporate natural language interfaces into their products, allowing users to interact using everyday language. Product-specific knowledge and prompt engineering enable foundation models to determine the appropriate API triggers and parameters. Microsoft Copilot [4] exemplifies this, and we can anticipate similar advancements, like Amazon's online store potentially offering a chatbot for streamlined tasks. Database providers like Oracle are already integrating natural language interfaces into their query engines [7].
Even before LLMs, chatbots were prevalent in customer service and support. Chatbots and chat apps can be used as agents for search engines or process orchestrations. LLMs significantly enhance their capabilities, fostering natural conversations, improved intent understanding, and effective resolution of complex queries. In customer service, LLM-powered chatbots handle a broader range of inquiries, offer personalized recommendations, and seamlessly escalate issues to human agents. Internally, chatbots or chat apps assist employees with IT troubleshooting, onboarding, and other tasks, optimizing IT team resources.
Recent AI advancements have spurred technology and business solution providers to enhance their products with pre-trained AI models. Reassessing your application and technology portfolio for strategic alignment can yield quick wins by replacing legacy products with AI-powered alternatives. Examples include payment solutions with real-time fraud detection, cybersecurity products with vulnerability and anomaly detection, and BI and data analytics platforms with built-in predictive analysis features.
The AI landscape abounds with readily available solutions offering immediate and tangible benefits. By embracing these opportunities, organizations can streamline processes, improve decision-making, elevate customer experiences, and gain a competitive advantage in today's rapidly evolving digital world.
Why Hiring for Adaptability and Learning Fuels Long-Term Success
In the fast-paced and ever-evolving world of technology, the traditional approach to hiring, which prioritizes "exact matches" to job descriptions, may be inadvertently stifling innovation and hindering long-term growth for organizations. While the comfort of a seemingly seamless onboarding process for candidates with identical skillsets and experiences is undeniable, the potential contributions of individuals with diverse backgrounds and a proven ability to learn and adapt should not be underestimated.
The "exact match" hiring strategy, often favored by hiring managers seeking a quick and efficient solution to fill vacancies, is rooted in the belief that candidates who have performed similar roles in the past will require minimal training and ramp-up time. This approach, however, overlooks the immense value that candidates from slightly different backgrounds can bring to an organization.
Firstly, individuals with diverse experiences and perspectives are more likely to introduce innovative ideas and challenge the status quo. Albert Einstein once said, "The measure of intelligence is the ability to change." In the context of the modern workplace, this suggests that employees who can adapt their skills and knowledge to new challenges are more likely to drive innovation and contribute to the long-term success of an organization.
Secondly, the "exact match" mentality can lead to a lack of diversity in the workplace, which can stifle creativity and hinder problem-solving. A study by McKinsey & Company found that companies in the top quartile for ethnic and cultural diversity on executive teams were 33% more likely to have industry-leading profitability[1]. This suggests that a diverse workforce, comprised of individuals with varying backgrounds and experiences, is more likely to generate innovative ideas and achieve superior financial performance.
Moreover, a homogenous workforce can lead to stagnation and a lack of fresh perspectives. Innovation often arises at the intersection of different cultures and disciplines, as individuals bring unique insights and approaches to problem-solving. By hiring candidates from diverse backgrounds, organizations can tap into a wider pool of knowledge and experience, fostering a culture of creativity and collaboration.
Finally, focusing solely on "exact matches" can result in missed opportunities to hire candidates with exceptional potential who may not have followed a traditional career path. For instance, individuals with strong backgrounds in computer science or other technical fields may possess the ability to quickly learn and adapt to new technologies and environments, even if they lack direct experience in a specific role. By prioritizing adaptability and learning potential, organizations can unlock hidden talent and foster a culture of continuous learning and growth.
In contrast to the "exact match" approach, hiring for adaptability and learning prioritizes candidates who demonstrate a strong ability to acquire new skills and knowledge, even if their backgrounds may not perfectly align with a specific job description. This approach offers several key advantages for organizations seeking long-term success.
Firstly, individuals with a proven track record of learning and adapting are more likely to thrive in a rapidly changing work environment. The World Economic Forum's "The Future of Jobs Report 2023" predicts that by 2025, over half of all employees will require significant reskilling and upskilling [2]. By hiring candidates who are comfortable with change and eager to learn, organizations can build a workforce that is prepared to navigate the challenges of the future.
Secondly, candidates from diverse backgrounds can bring fresh perspectives and innovative ideas to an organization. A study by Boston Consulting Group found that companies with above-average diversity on their management teams reported innovation revenue that was 19 percentage points higher than that of companies with below-average leadership diversity [3]. This suggests that a diverse workforce, comprised of individuals with varying backgrounds and experiences, is more likely to generate innovative ideas and drive business growth.

Finally, hiring for adaptability and learning can foster a culture of continuous learning and development within an organization. When employees are encouraged to learn and grow, they are more likely to be engaged and motivated, which can lead to improved productivity and retention. A study by Deloitte found that organizations with a strong learning culture are 92% more likely to develop innovative products and processes, 52% more productive, and 37% more profitable [4].
In today's rapidly changing world, the ability to learn and adapt is more critical than ever. Organizations that prioritize these qualities in their hiring processes are more likely to attract and retain top talent, foster a culture of innovation, and achieve long-term success. By embracing potential and looking beyond the limitations of the "exact match" mentality, hiring managers can unlock hidden talent and build a workforce that is prepared to navigate the challenges of the future.
This conclusion has significant implications for job matching engines like LinkedIn. These platforms should evolve beyond merely matching keywords and job titles. They should incorporate factors like learning agility, adaptability, and potential into their algorithms. This would enable them to identify candidates who might not have the exact experience listed in a job description but possess the transferable skills and the eagerness to learn and grow into the role. Such an approach would benefit both employers and job seekers, leading to a more dynamic and fulfilling job market.
Understanding the Composition of Access Control Systems
When it comes to building an Access Control System (Identity and Access Management, Entitlement Services, whatever) or selecting one of the vendor solutions in the marketplace, it is critical to understand what a sophisticated Access Control System should comprise and be clear about how each component is implemented. Any missing component could lead to risks and maintenance challenges.
The following is a general purpose architecture diagram for any access control systems.
This is a single, central access point for all access channels requesting to access any protected resources. As an analogy, it's like the single entrance to a library building protected by a security guard. You could design a system that has multiple access points - for example, some services provide endpoints directly reachable by access channels, and each service has its own guarding mechanisms in place. However, this approach can lead to security holes, inconsistency, increased costs, and maintenance challenges.
Access control decision is made in two processes:
For subsequent accesses, the aforementioned processes can be replaced by verifying a temporary permit e.g. an access token.
Authentication service refers to Identity Store - an Active Directory for example - to verify user credentials which includes multiple factors (MFA).
Authorization service exams the temporary permit and refers to the Policy Store to check all the applicable rules in order to make an YES or NO decision. The following diagram depicts a common authorization decision flow.
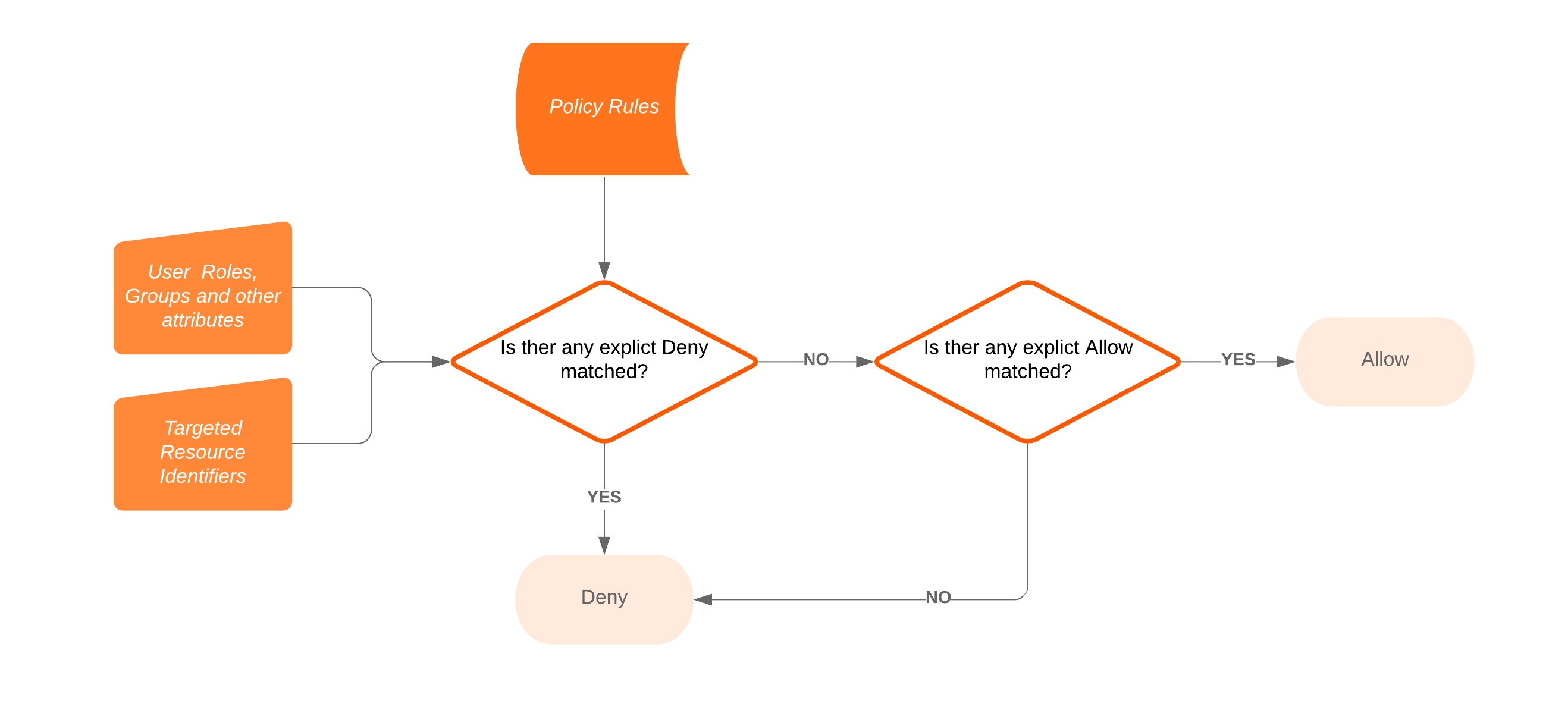
Information stored in a Policy Store includes:
This is the component that allows Administrators (via GUI) or Admin App (via APIs) to manage Identity lifecycle, grant or revoke permissions, register or de-register devices, and change policy rules.
All activities should be logged and monitored in real-time with proactive Alerts. Custom Reports can be generated from the logs for analytics and audit purposes.
An introduction to the architecture of AWS Lex Chatbot
Adding a highly engaging chatbot to your web sites can create immediate customer value. For example a support bot that helps your customers right on the spot can improve customer experience and enhance brand image. A support bot can be a customer support bot that serves external end users or a bot supports internal staff e.g. as a complement of IT Support team. The underline architecture should be the same for customer support bot and internal support bot.
From an architectural perspective, what I want to achieve in such a PoC exercise includes technology selection, assessment, feasibility analysis, understanding of the involved technology components/systems, and the attempt to piece them together to form an end-to-end solution. The detailed-level implementation - e.g., UI details, a complete and sophisticated Bot capability - which can be enriched on an ongoing basis - is not the focus of this PoC. Having said that, the PoC itself delivers a preliminary end-to-end solution.
Amazon Lex is an AI service for building conversational interfaces using voice and text with which developers can build applications with engaging user experiences and lifelike conversational chatbots. It is based on the same deep learning technologies that power Amazon Alexa. Under the cover, it utilizes automatic speech recognition (ASR) for converting speech to text, and natural language understanding (NLU) to recognize the intent of the text.
AWS Lambda is "serverless" technology meaning it lets you run code without provisioning or managing servers, although the code is still executed by a short-lived running environment - .e.g. a JVM instance inside a container. The more frequent the code is used, the faster instantiation of the running environments - they typically load up in milliseconds upon requests. AWS Lambda takes care of automatic horizontal scaling for up to 1000 concurrent running instances. With Lambda, you pay only for the compute time you consume - there is no charge when your code is not running. You can set up your code to automatically trigger from other AWS services or call it directly from any web or mobile app like calling a web service.
At a high level, this chatbot solution consists of three tiers: Client Channel, Conversational Interface and Intent Fulfillment Services.
The conversational interface of a chatbot is the "AI" portion which enables humanized conversation and identify the intent of a user. Based on the type of the intent, the interface will then collect all the parameters that are necessary to fulfill the intent. For example, "I want to order a pizza." would trigger a "Order pizza" intent, and "type of pizza", "size" and "delivery time" need to be collected for the client in order to fulfill the intent.
AWS Lex is an implementation of conversational interface.
Client Channel provides means for end users to interact with the bot. These typically include a browser, a mobile device and some messaging platform such as Facebook Messenger and Slack Channel.
AWS Lex supports the integration of five channels:
Intent fulfillment can be getting some information as a response - e.g. getting supporting information for a given application name - or performing some system actions - e.g. retrieving client's account balance.
Typically intents are fulfilled by calling back end services which include AWS Lambda functions and web services, or a combination of the two.
Facebook channel is a good choice for retail businesses. As most companies block social networking sites like Facebook, it is not ideal for clients accessing applications from their company network.
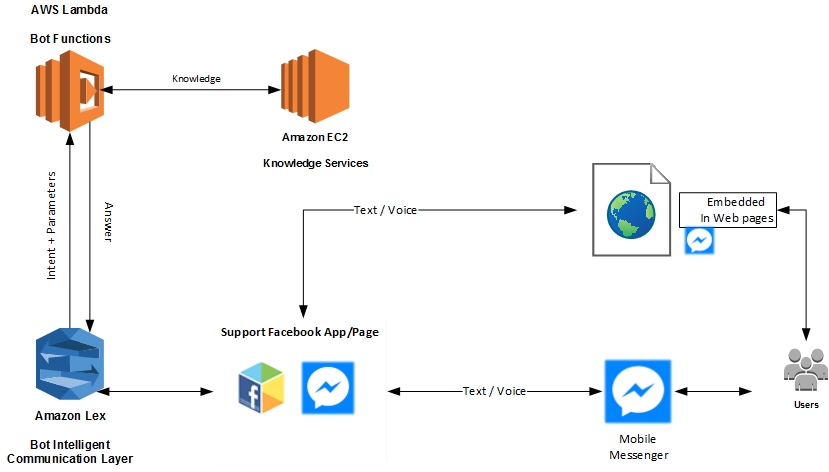
To integrate with Lex, a Facebook App is created which hooks up with a Facebook page for messaging via Messenger.
The diagram below depicts the high level architecture of Lex and Facebook channel integration.
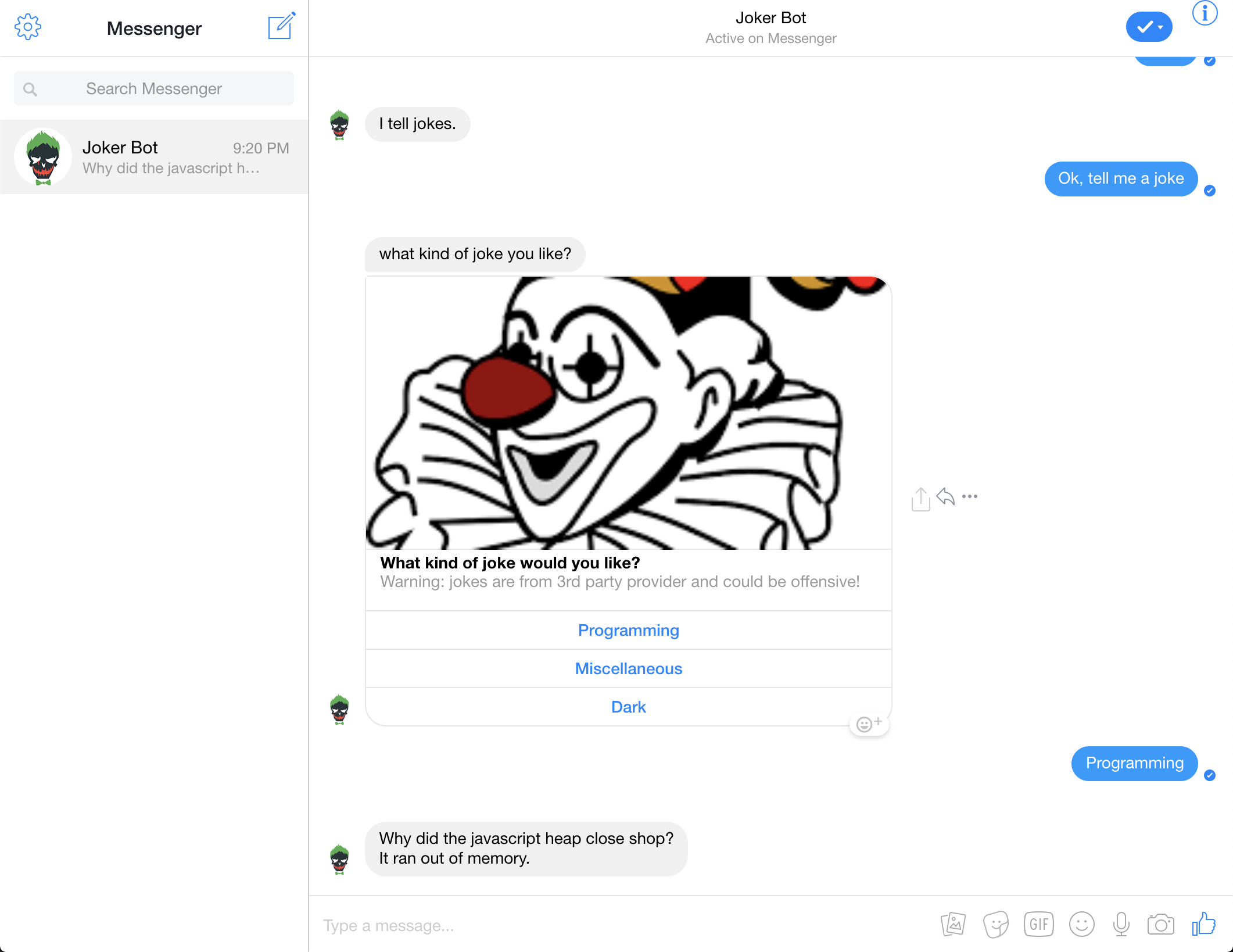
The screenshot belown shows channel integration with Facebook App which handles messaging via Messenger App.
The screenshot belown shows channel integration with Facebook chat plugin.
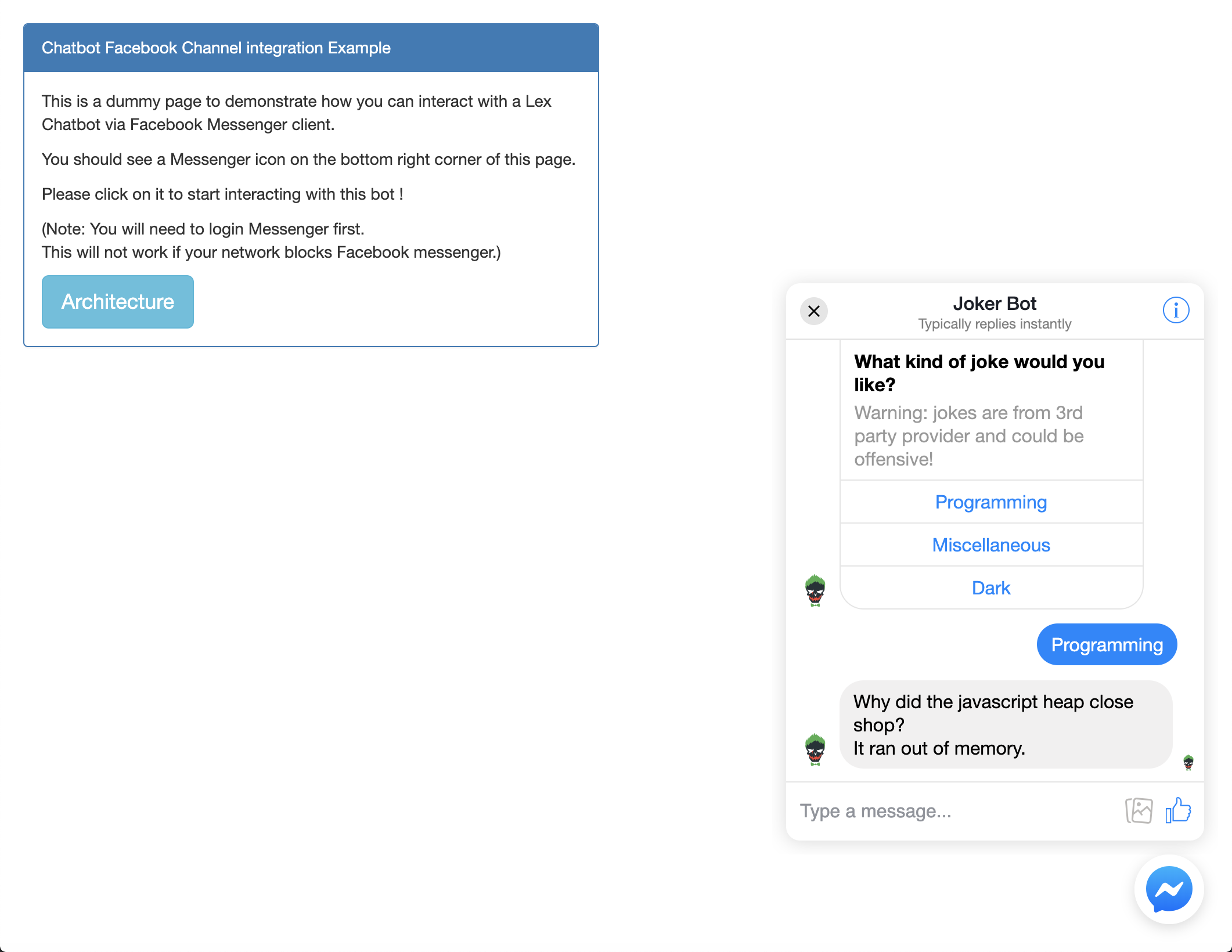
Web channel is more applicable to most use cases because it does not require an intermediate messaging layer, however more development work is required in order to communicate with Lex directly. Amazon Cognito is used for user login for this PoC.
The diagram below depicts the high level architecture of Lex and web channel integration.
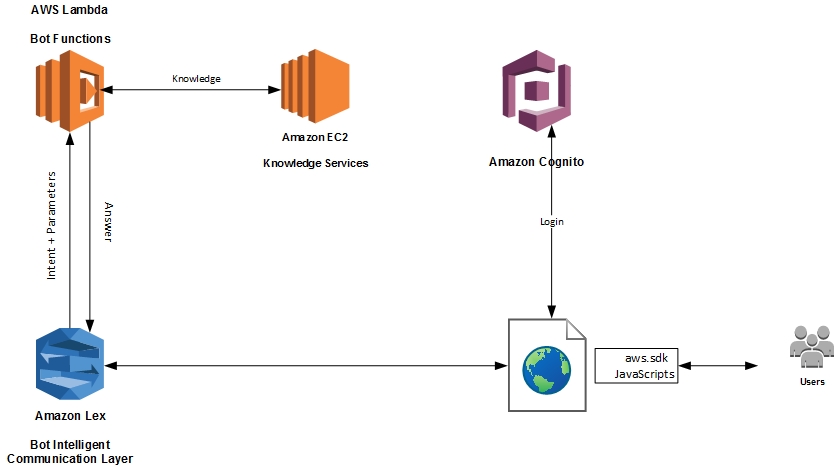
The screenshot belown is from a sample web page with web channel integration.
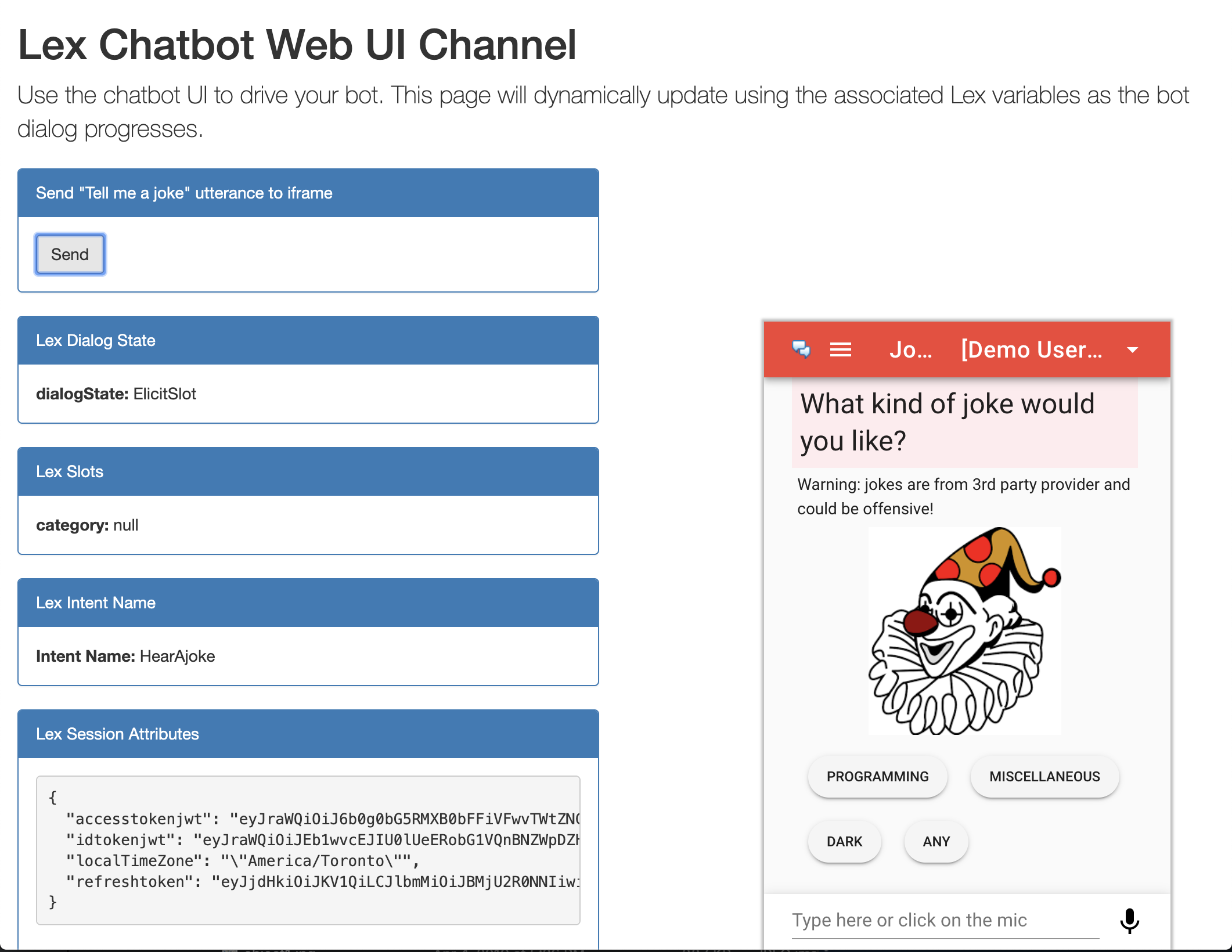
The back-end intents and fulfillment services can be enhanced and deployed independently of the web client channel. The web channel component can be deployed as an independent web application and can be embedded in parent web sites using HTML iframe. What sites (internal or external) can host and/or embed this bot (CORS) is configurable for security control.
A humanized conversational support bot could quickly enhance client experience and service satisfaction. AWS Lex and AWS Lambda can be leveraged to implement an end-to-end cost effective support bot solution. With the proposed architecture, developers can simply focus on creating robust fulfillment services. The capability of the support bot can be expanded gradually as new intents and respective fulfillment services can be added along the way.
Where do we draw the line between coarse-grained and fine-grained access control?
It can be confusing when people talk about IAM and Entitlement, and it can be even more confusing when people use the terms “coarse grained entitlement” and “fine grained entitlement”, which can mean different things to different people. This article attempts to clarify the core concepts in the realm of IAM and Entitlement Management so that people can ask right questions in order to be on the same page.
IAM consists of two parts – Identity Management and Access Management. These two parts go hand-in-hand because authentication (login) depends on Identity.
Identity Management provides a central repository—hence the single source of truth—to create, store, and maintain user profile information, including Global Unique Identifiers, organizational information, roles and job functions, credentials, and any other attributes that describe such a user account. The Identity repository is usually backed by an LDAP-compatible directory service. The Identity Management component should provide two functions: Identity Lifecycle Management and Profile Management. Sophisticated IAM solution providers offer both a GUI (usually an out-of-the-box web-based UI) and APIs to enable these two functions.
Typical Identity lifecycle consists of the following stages - they have impacts on validity and the status of the Identity itself.
Some IAM providers provide user self-enrollment feature so that Identity admins only need to review, verify and approve enrollment requests.
Identity Profile Management is the management of user attributes that do not impact the validity and the status of the Identity. Some of the attributes can be managed by user themselves and some of the attributes are locked down and can only be managed by Identity admins.
Profile information is critical for downstream applications. Some organizations have more restrictive control over Identity Management—for example, they require a maker-checker rule on the client onboarding process, hence introducing another buzzword, “Identity Governance.” Essentially, it is just the separation of duties among Identity admins; e.g., some admins can create new IDs but can’t activate them, and some other admins can activate them but can’t create them.
Before the system can determine what you have access to (Authorization), it has to determine whether you really are who you claim you are (Authentication).
A decade ago it is sufficient to prove you own the Global Unique Identifier if you know its associated password, nowadays, to meet the regulatory requirements, in addition to the password, another secret (2FA) or more than one other secrets (MFA) much be provided to identify yourself.
Modern IAM providers must provide the following features:
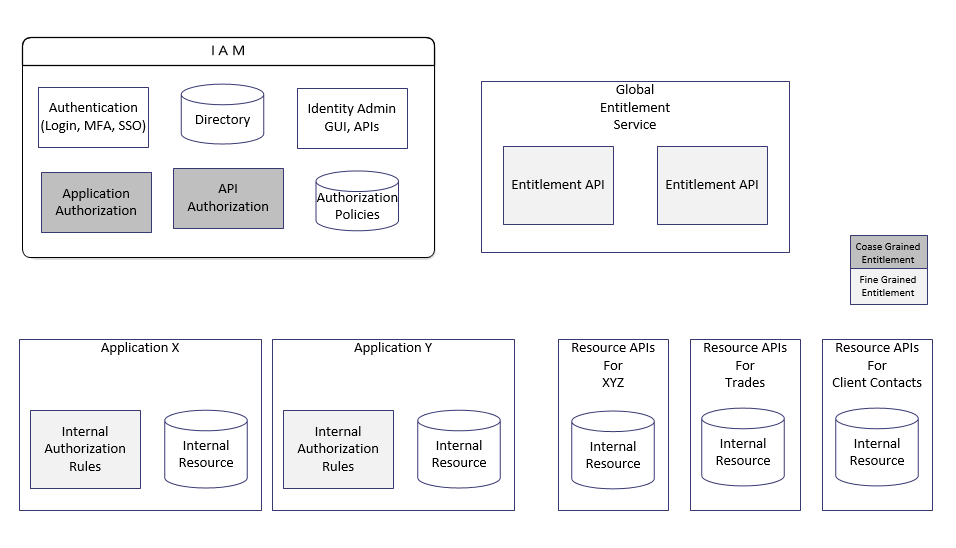
Authorization is the most confusing part. Is it simply another word for Entitlements? In general, Authorization, or Entitlement, can be divided into the following three levels
Here, an application means a web-based system that provides user interfaces backed by services—for example, an online banking application. If a user is not authorized to access the application, access the entire application—all the resources the application can offer. There are two ways to block unauthorized access:
Here, a Resource API means a web-based application without user interfaces; it returns or processes data in the back end. For example, a User Profile API can provide create/read/update/suspend operations to user admin modules. This definitely qualifies for coarse-grained entitlement. Whether it can be considered fine-grained entitlement really depends on how granular the resource APIs are. Most modern IAM solution providers — Centrify and Okta, for example — support this level of access management.
Objects within applications and rows within databases are internal to applications; hence, access control on these resources must be considered fine-grained entitlement. IAM, as an independent external system, has no means to access or control access to these internal resources; therefore, object/row-level access control is NOT in the scope of IAM. If any IAM providers claim they support fine-grained entitlement management, ask them the right questions.
Having said that, there is nothing stopping us from centralizing and storing attributes that can be used to drive object/row-level access control in user profiles within the IAM directory. IAM can simply pass this information on to the targeted applications as assertions for fine-grained decision-making. Alternatively, and as a best practice, applications should externalize such decisions to a central Entitlement Service (again, not IAM), provided the application has the ability to interact with such an Entitlement Service.
IAM and Entitlement Management can mean different things to different people, hence they can be confusing. In general, the following diagram depicts their scopes.
What can we learn from Laozi in today's competitive world?
Laozi (6th–5th century BCE), the founder of philosophical Taoism, touched on the subject of 争 (closest translation: competition, contention) in a few places in his main work Tao Te Ching about how "the Way" (Tao) of the sage would behave when confronting competitions. The one I like the most is the following (in Chinese):

The closest translation I can find, without losing the core of its meanings, is the following:
My interpretation is that Laozi believes a good person does not contend. A good person only competes with himself or herself to keep getting better. A person gets credit when credit is due. This is also applicable to a team, a company, and a nation. A company should focus on making its own products and services better rather than using any other tricks to gain competitive advantages.
A user story of Virtual Reality and Augmented Reality
In a Friday evening in 2030, Chenglian was reminded that it was about time to play squash with his brother again. Chenglian’s brother lives in China and he has invited Chenglian to play squash with him every Friday evening. Chenglian lived in a small apartment in Toronto downtown core. Standing in the middle of his living room, he put on his glass and saw his brother was in the squash room and waving to him. They greeted to each other first and started talking about some new innovation ideas Chenglian’s brother has been thinking about in the past few days. Chenglian then picked up his new squash racket, a new product by InnoSport INC, and threw a 3D visual copy to his brother. Chenglian’s brother pulled the 3D copy of the racket over and took a 360 degree look. Chenglian recommended to his brother that this new model from InnoSport delivered the best simulation during the play. The feedbacks of the angle and resistance produced by the racket feels just like real. Chenglian’s brother was impressed and agreed to order one as well.

After that, they started playing. Chenglian moved left and right, forward and backward, and swung his racket, smashing the ball like he used to do in the gym many years ago. They could see each other’s moves and the direction of the virtual squash ball, and hear the noise of their shoes sliding on the floor. The virtual referee made announcements whenever one of them scored. After five minutes, Chenglian started sweating and breathing heavily. The referee announced that Chenglian had burned 125 calories and his brother had burned 135. They took a break and laughed together as it was still far from their goals. Chenglian and his brother enjoyed the time playing squash together not only because they could burn calories, but also because they could see each other and share news periodically – even though they lived 8000 miles apart.
A business design idea that allows sport fans to see from their stars' POV, in real-time.
This is an imaginary TV commercial (even the domain name is fabricated), as an exercise of innovation and business design, compiled using many video clips found in Youtube.com. The background music is 'Dirty Paws' by Of Monsters and Men.
Innovation without fun is no fun.

Designer Dominic Wilcox created the Finger-nose Stylus so he could use his touchscreen phone in the bath hands-free. The stylus can also be used for less hazardous functions, like keeping hands free for multitasking. It also sets your hands free when you wear groves in the winter. And it does not make noise!
Dr Michio Kaku on the future in 5 to 20 years
Dr Kaku made many predictions, some of which are based on IoT though he didn’t explicitly use the term “IoT”. Here is a few interesting (though not entirely new) predictions:
Are cryptocurrencies bubbles or future reality? Shall we invest now?
I raised this question after watching the videos in response to "Kraken Investment Case Competition 2016".
Bitcoin vs Ethereum: You have $1M to invest across these two blockchain technologies by buying bitcoins and ethers – the digital assets or “cryptocurrencies” that power these decentralized computer networks. You cannot touch your investment for the next 5 years. How much of that $1M do you invest in each? Why?
I would vote for the Ivy team. With the current state of cryptocurrencies, I would not recommend to invest unless you are an extreme gambler.
The idea of digital currency is rather old. Any online service providers can issue their own digital currencies that are acceptable within their platform. For example, many online gaming companies issue their game currencies in different terms - points, coins, golds, weapons, etc. - for players to buy using real money in order to gain access to features and competitive advantages. Some gaming platforms allow players to collect game currencies as rewards and transfer to other players - mostly to exchange with real money.
The contemporary cryptocurrencies are different from the traditional digital currency for two major characteristics:
Bitcoin, the first Cryptocurrency was invented in 2009 by Satoshi Nakamoto, who still remains anonymous. The technology is open-sourced meaning anyone can create a new Cryptocurrency that works in a similar way. The second most influenctial Cryptocurrency is Ether, which runs on Ethereum public Blockchain. Ethereum was invented in 2013 by Vitalik Buterin, a Canadian programmer, and went live in 2015. From a technology perspective, Ethereum is more valuable in that the idea of Smart Contract is a revolutionary of Blockchain technology.In my opinion, it is as important as the idea of World Wide Web. Both Cryptocurrencies require some form of mining for the distribution of the currencies. The total number of Bitcoin is 21 million including those have not been mined. Satoshi Nakamoto keeps 7.5% (21,000,000 X 0.075 = 1,575,000 Bitcoins) of the Bitcoins for himself/herself/themselves. Bitcoin is highly divisible - the smallest unit is called Satoshi representing 0.00000001 Bitcoin. The main cost of the mining activity is electricity - which can be surprisingly huge. Satoshi Nakamoto has designed that the mining process would get harder and harder as more Bitcoins have been discovered. This creates incentives for miners to start mining earlier. It also implies that the value of Bitcoin will get higher and higher - no miner would be interested in mining the new ones if the mining cost surpasses the value of the new Bitcoins.
The history of human civilization is essentially a history of efficiency creation. The trend of moving from inefficiency towards efficiency is unstoppable although it could possibly be slowed down by particular individuals and groups from time to time. If you agree with this, like myself, then you would agree that Cryptocurrency will be FUTURE reality - I don't think it is NOW, simply because none of the major retailers (e.g. Amazon, Alibaba, eBay, etc.) has started accepting it. P2P money transfer is apparently faster and cheaper than relying on a third party like a bank as the trusted authority, left aside the privacy issues. In an ideal world, one unique cryptocurrency is accepted by all human beings and the amount of the cryptocurrency each individual owns fairly represents his or her wealth. We live in a global economy and the future of the world will be a global village (nationalists might disagree.). If one currency works, why would we need two? You might be confused and wondered whether this contradicts to the ideology of democratization. Think again.
Bitcoin and Ethers are the two main players currently. There are others and there will be more to come. Even the same Cryptocurrency can be forked to another copy resulted in two very similar Cryptocurrencies - this happened to Ethereum in 2016. Simply put, the creation of a new Cryptocurrency is almost instant and with no cost. Bitcoin somehow managed to convince the community to use it as the backup currency for all other Cryptocurrencies - you can only use Bitcoin or real money to buy other Cryptocurrencies. This move essentially makes Bitcoin the "Reserved Currency" of Cryptocurrencies - very much like using Gold and USD as the reserved currency for other currencies. However, Bitcoin Blockchain has encountered underline design problems - new transactions take too long to be verified by the chain. Who will be the ultimate winner? I don't know.
Institutional investors can profit from volatility by using a variety of hedging techniques. I imagine this would be applicable to Cryptocurrency exchange centers as well. However, for normal investors, volatility is bad. All currencies fluctuate in their values, but in completely different ways from how Cryptocurrencies do. Real currencies fluctuate in value based on the market risk dynamics and do not dramatically deviate from the underline value - the buying power. The price of Cryptocurrencies fluctuates based on nothing because nobody knows how to value it. One policy change from one authority could wipe off 50% of its value in one day. Until most people in the world start accepting cryptocurrencies and measure their values with real goods and services, their values are completely subjective to speculations. If Bitcoin would replace all currencies in the world, one Bitcoin would worth about one million USD. If Bitcoin loses, then it would worth zero, in theory. Cryptocurrency exchanges don't care as long as they can charge fees, in real dollars. The vast majority of bitcoin transactions happen in exchange centres not retailers. Speculators don't care as long as the Cryptocurrencies don't stuck in their hands.
Then the initial distribution of the Bitcoins becomes questionable. And as an example, Satoshi Nakamoto would have the power to control the world economy. Would all countries allow this to happen? In theory, you can run a private organization that has Bitcoin mining factories all over the planet, in an attempt to control vast majority of the wealth in the world. Currently people spend too much efforts on mining and speculative trading. What we should really do is to promote Cryptocurrency adoption through the collaborations of all nations in the world. Yes, it is hard - easier said than done.
Though Cryptocurrency will be an important part of human civilization, the ultimate future unique or dominant Crypotocurrency remains uncertain. Currently their values are purely driven by speculations. Therefore, I would not consider them as investible assets for serious investors.